File Security
Multi Commander's File Security tools provide comprehensive Windows file system permissions management, enabling secure access control, ownership administration, and permission configuration for files and folders. These powerful administrative tools require elevated privileges but offer complete control over file system security through an intuitive interface integrated into the file management workflow.
Advanced File System Security Management
Take complete control of file and folder permissions with enterprise-grade security tools. Manage ownership, configure access rights, and implement security policies directly within Multi Commander's familiar interface while maintaining full Windows security model compliance.
Windows File System Security
Windows file system security relies on Access Control Lists (ACLs) that define who can access files and folders and what operations they can perform. Multi Commander's File Security tools provide direct access to these powerful security mechanisms through an intuitive interface.
Security Components
Ownership Control
- File Ownership: Control who owns individual files and folders
- Administrative Takeover: Assume ownership of inaccessible files
- Inheritance Management: Control ownership inheritance for subdirectories
- Security Descriptor Control: Manage complete security metadata
Permission Types
- Read Access: View file content and properties
- Write Access: Modify file content and attributes
- Execute Access: Run executable files and access directories
- Full Control: Complete access including permission modification
Accessing File Security Tools
File Security tools are located in Multi Commander's Tools menu and require administrative privileges to function. Running Multi Commander as Administrator is necessary for these operations to succeed.
Tools Menu Location
Navigation Path
Navigate to Tools → File Security to access the complete suite of security management utilities.
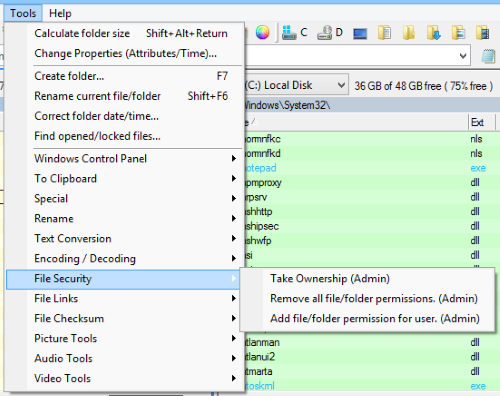
Tools menu showing File Security submenu with administrative permission management options
Available Operations
- Take Ownership (Admin): Assume ownership of selected files and folders
- Remove all file/folder permissions (Admin): Clear all permission entries
- Add file/folder permissions for user (Admin): Grant specific access rights
Administrative Requirements
Privilege Requirements
- Administrator Rights: All security operations require elevated privileges
- Multi Commander as Admin: Launch Multi Commander with "Run as Administrator"
- UAC Considerations: Windows User Account Control may prompt for confirmation
- Network Limitations: Some operations may not work on network resources
Safety Considerations
- Backup Important Data: Always backup before major permission changes
- Test on Sample Files: Verify operations on non-critical files first
- Document Changes: Record permission modifications for audit purposes
Ownership Management
File ownership determines who has ultimate control over files and folders, including the ability to modify permissions and grant access to other users. Taking ownership is often necessary when recovering access to orphaned or inaccessible files.
Take Ownership
Ownership Transfer Process
The Take Ownership operation transfers ownership of selected files and folders to the current user account:
- Selection: Select the files or folders requiring ownership transfer
- Execution: Choose "Take Ownership" from the File Security submenu
- Processing: Multi Commander applies ownership changes to all selected items
- Verification: Confirm successful ownership transfer through file properties
Common Ownership Scenarios
- Orphaned Files: Files with deleted or invalid owner accounts
- Access Recovery: Recovering access to files with restrictive permissions
- Administrative Takeover: Assuming control of system or user files
- Migration Recovery: Correcting ownership after system migrations
Ownership Benefits
- Permission Control: Ability to modify file and folder permissions
- Access Restoration: Restore access to previously inaccessible files
- Administrative Control: Complete management authority over file resources
- Security Management: Implement security policies and access controls
Ownership Implications
Legal Considerations
- System Files: Taking ownership of system files may affect system stability
- User Data: Respect privacy and legal requirements when accessing user files
- Corporate Policies: Follow organizational guidelines for file access
- Audit Requirements: Document ownership changes for compliance
Technical Impact
- Permission Inheritance: May affect how permissions are inherited by subfolders
- Application Access: Some applications may require specific ownership patterns
- Service Dependencies: System services may depend on specific file ownership
Permission Management
Permission management controls who can access files and folders and what operations they can perform. Multi Commander provides tools to both remove and add permissions with granular control over access rights.
Remove All Permissions
Complete Permission Removal
This operation removes all permission entries from selected files and folders, effectively denying access to all users and groups:
- Total Lockdown: No user or group will have any access to the files
- Including Owner: Even the file owner loses access after this operation
- Inheritance Clearing: Removes both explicit and inherited permissions
- Recovery Required: Use "Add Permissions" to restore any access
Critical Warning
After removing all permissions, NO ONE will have access to the affected files. You must use the "Add Permissions" command to restore access, or the files will remain permanently inaccessible.
Use Cases
- Security Lockdown: Secure sensitive files by removing all access
- Permission Reset: Clear complex permission structures for rebuilding
- Quarantine Files: Isolate potentially dangerous files
- Access Control Testing: Verify application behavior with no file access
Add Permissions
Permission Assignment
The Add Permissions tool provides granular control over user and group access rights:
- User-Specific: Grant permissions to individual user accounts
- Group-Based: Assign permissions to security groups
- Permission Levels: Choose from read-only, read/write, or full control
- Everyone Access: Grant permissions to the "Everyone" group for universal access
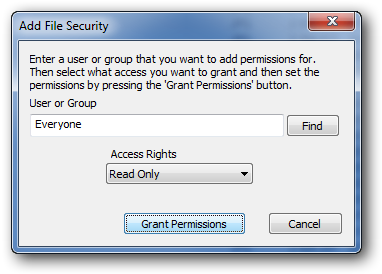
Add Permissions dialog showing user selection and permission level options
Permission Types
- Read-Only: View file content and properties without modification rights
- Read/Write: View and modify file content and basic properties
- Full Control: Complete access including permission modification
- Custom Permissions: Advanced permission combinations for specific requirements
Advanced Features and Custom Commands
Beyond the basic permission management tools, Multi Commander's security capabilities can be extended through custom commands and scripting for automated security administration workflows.
Custom Command Integration
Security Automation Commands
Integrate security operations into custom commands for automated administrative workflows:
// Take ownership of selected files
MC.Utils.TakeOwnership FILES="${selectedfiles}"
// Remove all permissions from files
MC.Utils.RemovePermissions FILES="${selectedfiles}" RECURSIVE=1
// Add read/write permissions for current user
MC.Utils.AddPermissions FILES="${selectedfiles}" USER="${currentuser}" RIGHTS="ReadWrite"
// Grant full access to Everyone group
MC.Utils.AddPermissions FILES="${selectedfiles}" USER="Everyone" RIGHTS="FullControl"Workflow Integration Scenarios
- Automated Security Hardening: Apply consistent security policies to file collections
- Migration Scripts: Correct permissions after system migrations or deployments
- Incident Response: Quickly secure or quarantine files during security incidents
- Compliance Automation: Implement organizational security policies systematically
Security Management Strategy
Master file system security by combining Multi Commander's tools strategically: use ownership takeover to regain access to orphaned files, implement the principle of least privilege when adding permissions, and leverage custom commands for consistent security policy enforcement. Always backup critical data before making significant permission changes, and document modifications for audit and troubleshooting purposes. This systematic approach ensures robust security while maintaining operational efficiency.
Related Security Tools
Enhance your file security workflows with related features: File Checksum Tools, Change File Properties, Custom Commands Reference, and Find Opened/Locked Files.